181 xxxx-xx-xx xxxxxx INFO lots of textRITM1234FAILED BECAUSE ROOT. The sequence of search-time operations.
Automatically Find And Build Event Types Splunk Documentation
The results will be the most recent events by default because splunk returns events in time order unless explicitly sorted.
. The Generate Events function is configured as follows. 1 host 2 source 3 source type 4 index and 5 timestamp. This constraint is what an experienced Splunk user might think of as the first portion of a search before the pipe character commands and arguments are applied.
Splunk software supports event correlations using time and geographic location transactions sub-searches field lookups and joins. When a build is complete succeeded or failed all announced events will have been posted. Please note that not all parent events of a child event must necessarily be posted before it.
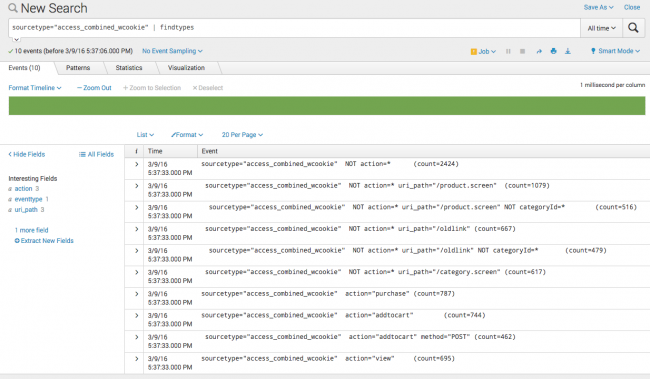
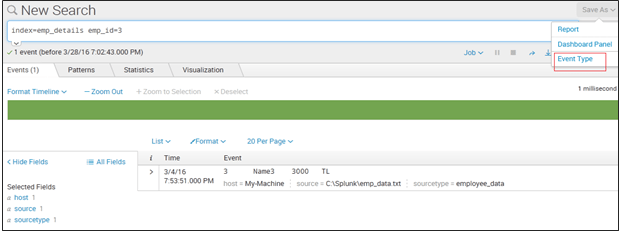
Click Event Actions and select Build Event Type. The Generate events function is. Below is how my log prints.
Join data champions from around the globe for empowering sessions compelling keynotes and guest speakers peer connection opportunities and tons of conf fun. The Generate Events function is configured as follows so that it generates 20 events where the body field contains the value key0value0 and the host field contains the value test-host-1. These knowledge objects include extracted fields calculated fields lookup fields field aliases tags and event types.
Hence i would require some support to build search query. You need to get the first 3 events after a particular event for example a login event for the events related to a particular user but there is no well-defined ending event. Fields appear in event data as searchable name-value pairings such as user_namefred or ip_address19216811.
In order to extract fields from either sidebar event lists or the settings menu using UI. EY Turns Data into Doing. Different events from different sources from the same host.
June 13 - June 16 2022. Las Vegas and Virtual. Fields are the building blocks of Splunk searches reports and data models.
Run a search that returns events that you want to base an event type on. In above scenario expected results would be like below. Build resilience to meet todays unpredictable business challenges.
Look at the following example search. Optional Change the Destination App value to the correct app for the event type if it is not your current app context. Adding a new event type in Settings.
There are 5 default fields which are barcoded with every event into Splunk. I happened to check my logs for this problem today and found 81 events in the last 24 hours. Enter the Search String for the event type.
By the way to provide a minor update to the first post the network traffic data model build has completed and is at 100. Different events from the same source and the same host. Select Settings Event Types.
In case of a Bazel crash or a. Hi Im trying to build a query to get the count of opened and resolved incidents every hour in a day but the numbers are not tallying. The event contains a number of fields but two key ones are StepName and Timing.
Provide a unique Name for the event type. Every build event except for the initial build event has one or more parent events. 17 Explain default fields for an event in Splunk.
This search consistently returns a specific kind of event. This documentation applies to the following versions of Splunk. I still have the issue.
Not sure if the issue might be the fact that ServiceNow uses GMT and therefore all the tickets have the dv_opened_at and dv_closed_at field in terms of GMT and the _time field is the local time which in my case is EST. Identify an event in the results returned by the search that could be an event type and expand it. StepName will be a title for the HTTPRequest etc.
You can search for related events and group them into one single event called a transaction sometimes referred to as a session. The Build Event Type utility or Event Type Builder leads you through the process of creating an event type that is based on an event in your search results. Track a series of related events which may come from separate IT systems and data sources together as a single transaction.
For example status 600 and sourcetypeaccess_ OR sourcetypeiis are possible event dataset definitions. Timing will be a int value of the milliseconds taken by HttpRequest. When you run a search on your event data Splunk software looks for fields in that data.
Root event datasets are typically defined by a simple constraint. Please correct me if Im wrong. With the help of event correlation an intrusion detection system could recognize these related events as a potential cyberattack and alert the appropriate team.
Identify and group events into transactions. An event correlation tool can map and contextualize the data it ingests from infrastructure sources to identify suspicious patterns in real time. All events appear at random time intervals with an average of 15 events for each occurrence.
Finding Events After Other Events Problem. Not sure what changed but all of a sudden on one of our Splunk boxes Im getting errors when navigating and for screens that do happen to work the COVID-19 Response SplunkBase Developers Documentation. When you run a search Splunk software runs several operations to derive various knowledge objects and apply them to the events returned by the search.
18 How can you extract fields. Splunks most anticipated customer and partner event of the year. I have a script which sends individual events into Splunk each event is essentially a report on a HTTP Request either GET or POST.
Generate static value events. The more interesting case is fixed duration queries. Focus on high fidelity threats to your environment with Event Sequencing in Splunk Enterprise Security and accelerate time to investigate and respond to incidents.
I am new to Splunk. I want to retrieve corrId ex- corrId12345 dynamically from one event api logby providing apiName and build splunk search query based on retrieved corrId value that means it will pull all the event logs which contains same corrId corrId12345. All build events form a directed acyclic graph through their parent and child relationship.

Using Events Lists Splunk Documentation
Knowledge Objects Splunk Events Event Types And Tags By Aayushi Johari Edureka Medium

0 Comments